My friend Michelle recently explained to me that password is a perfectly valid password to use. Her reason? “People always say not to use it. So now that nobody uses it anymore, it’s totally secure again!”

How I’d Hack Your Weak Passwords
In this case, Michelle made a fatal assumption. She assumed that human beings would be manually typing in guessed passwords. What she failed to understand is that it’s really, really easy for any off-the-shelf computer to chew through possible passwords at an incredible pace.
You know where they start? With password.
In an article written for Lifehacker entitled How I’d Hack Your Weak Passwords, author John Pozadzides says the following:
If you invited me to try and crack your password, you know the one that you use over and over for like every web page you visit, how many guesses would it take before I got it?
Let’s see… here is my top 10 list. I can obtain most of this information much easier than you think, then I might just be able to get into your e-mail, computer, or online banking. After all, if I get into one I’ll probably get into all of them.
Your partner, child, or pet’s name, possibly followed by a 0 or 1 (because they’re always making you use a number, aren’t they?)
- The last 4 digits of your social security number.
- 123 or 1234 or 123456.
- “password”
- Your city, or college, football team name.
- Date of birth – yours, your partner’s or your child’s.
- “god”
- “letmein”
- “money”
- “love”
Statistically speaking that should probably cover about 20% of you. But don’t worry. If I didn’t get it yet it will probably only take a few more minutes before I do…
Everything you know (about passwords) is wrong
Michelle and I share a cell phone plan. The other day, she asked me for the account info so that she could login and do some stuff. So I gave her my information (because I trust her).
- Username:
[email protected] - Password:
cVWXDD$XkA25eZo437F£$^Xp(not my real password)
She flipped-out on me. “Who’s going to try to hack into your AT&T account?!” I tried to explain how that wasn’t the point, but she’d already moved on to the next shiny object.
I talked a couple of months ago about how I’d changed every single password I have. Why? Because I was re-using the same passwords all over the place, and it was time to fix that.
In short, one of my hard-to-guess-but-used-in-lots-of-places passwords was one of the ones that was obtained by hackers. As such, I had the fine work ahead of me to change the password for every single site that used the password that got hacked.
1Password to the rescue! It took me about 90 minutes, but I was able to lookup all of the sites where this password was being used, and change the password for all of them. This event ended up making me re-think how I managed my passwords.
It’s not that anybody would care about my AT&T account. It’s that if I re-use the same password across multiple websites, it increases the likelihood that if a site gets hacked, that they can use that information to access other sites where you use that password.
We need to start doing a better job
Going back to the piece by John Pozadzides:
You probably use the same password for lots of stuff right?
Some sites you access such as your Bank or work VPN probably have pretty decent security, so I’m not going to attack them.
However, other sites like the Hallmark e-mail greeting cards site, an online forum you frequent, or an e-commerce site you’ve shopped at might not be as well prepared. So those are the ones I’d work on.
So, all we have to do now is unleash Brutus, wwwhack, or THC Hydra on their server with instructions to try say 10,000 (or 100,000 – whatever makes you happy) different usernames and passwords as fast as possible.
Once we’ve got several login+password pairings we can then go back and test them on targeted sites.
But wait… How do I know which bank you use and what your login ID is for the sites you frequent? All those cookies are simply stored, unencrypted and nicely named, in your Web browser’s cache.
Any moderately-determined person could figure out how to hack passwords.
Normally, when you sign-up for a service, they don’t actually store your password. Instead they store a one-way hash of your password. What does this mean?
- Real password:
monkeyfarts - Hashed password (SHA–1):
a05727a789efdeaaa0b3f45e7f944c1f17691da6.
This way, they don’t know your password (yay, security!), and since it’s a one-way hash, they can’t figure out your real password if all they have is the hashed password.
But here’s the problem: If someone were to get a giant list of hashed passwords, there are enough pieces of the puzzle there to be able to begin figuring out common password patterns.
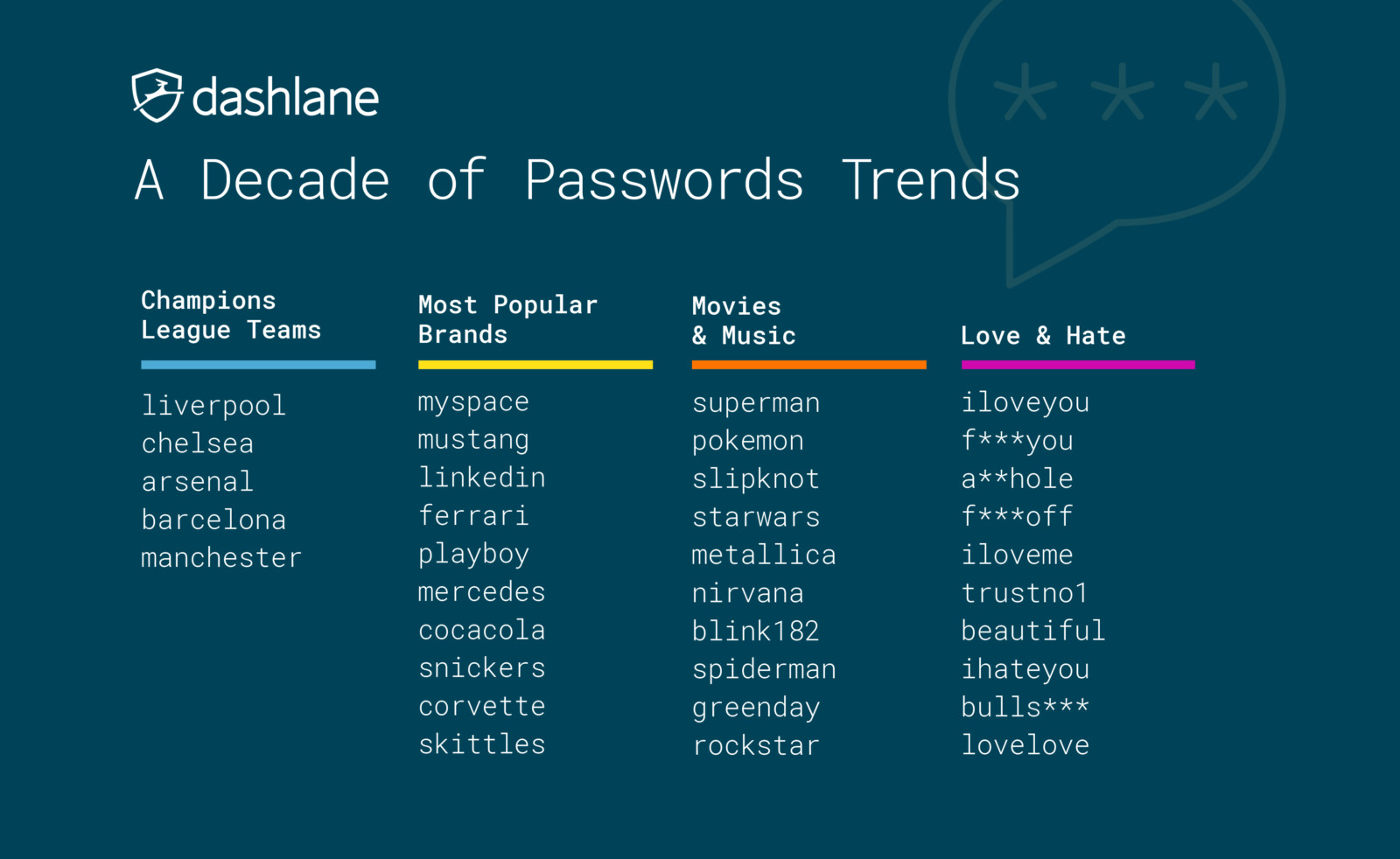
This is what happened in 2009 when a site called RockYou got hacked and a giant (32.6 million) list of usernames and hashed passwords were stolen. (RockYou makes fun little things for Facebook, and used to make fun things for MySpace. There’s a very good chance that you’ve used something they’ve done.)
In Brief Analysis of RockYou Passwords, we learn:
Dictionary passwords, that is, words like “password,” “monkey,” and so on, make one of the most stable groups.
Digital passwords based on easily memorized numeric combinations, phone numbers, document numbers, birth dates, and more make another group, which is as stable as the previous one, and maybe even more popular.
Passwords based on names and their derivatives. For example, a user may use the name of himself, his pet, some city, some place, and so on.
Passwords based on keyboard combinations, such as “abc123,” “qwerty,” etc.
Emotional passwords, such as “iloveyou,” “hateu,” “lovely,” “ihatemyboss,” or “ILoveJohn.”
[…]
Curiously enough, some users choose obscenely long passwords consisting of more than 20 characters, word combinations, or phrases. Here are some of these wonderful passwords (did you really think that nobody knows what you are typing?):
Hahaithinkilovejessebutthenagainmaybenotcuzheisadiknob
Lets you come back for your Countdown Timer
me plus food equals more sleep each night
tommmmmmmmmmmmmmmmmmmmmmmmmmmm
truongcaodangcongdonghaiphong
icantbelievethisshit.12345
banditbanditbandit1bandit1bandit1banditbandit
11111111111111111111111111111111111111111111
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
FUCKSCHOOLANDALLTHETEACHERSINIT
ilovepalmermyfuturehusband
1delightyourselfinthelord!
Imaprincessbecausemyfatheristheking
iluvanjabisset4evashesmawebaexxx
stuartandchrisrmybestmatesforeva
thisismypasswordyoullnevergetit
Just for fun, I downloaded a copy of hashcat and the rockyou.txt list of hashed passwords. Within 30 minutes, I’d managed to crack several thousand passwords from the list.
This is not hard to do.
Okay, okay. What should I do differently?
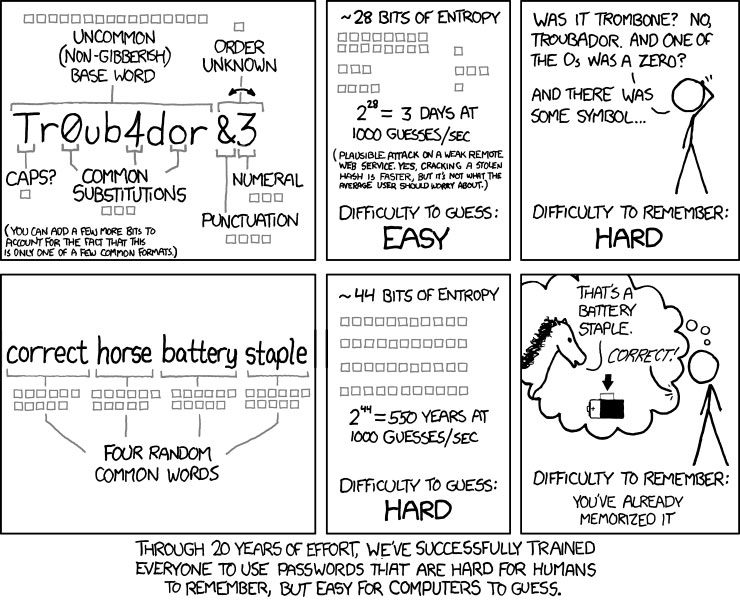
First of all, if you’re using password as your password, you’re fired.

-
Don’t use a word that can be found in the dictionary.
-
If you choose to use a word, replace some of the letters with numbers or special characters. (Instead of
monkeyfarts, usem0ñKeyƒår†s.) -
The longer the password, the better. Most sites require a minimum of 6 characters. I’d say to use a minimum of 10 characters. (Most of mine are in the 24–32 character range.)
-
Don’t use the same password twice. I know this may seem hard, but let’s get to the next bullet-point.
-
Stop trying to memorize your passwords. Let a password manager do it for you. 1Password, LastPass and Password Safe are all good solutions.
-
Enhance your passwords with a second level of security. If a service you use supports Two-Factor Authentication (or Multi-Factor Authentication), enable it. This way, even if your password gets hacked, they won’t be able to access your account without a special code that only you have.
- Lots of services are adding support: App.net, Apple, Amazon Web Services, Dreamhost, Dropbox, Evernote, Facebook, GoDaddy, Google, Microsoft (including Hotmail, MSN & Xbox Live), Paypal, Stripe.com, Yahoo!, WordPress.com (including Gravatar), and more!
If you’re worried about someone (perhaps someone you know) figuring out your password and using it for nefarious purposes (including simply violating your personal privacy, e.g., checking your messages, reading your emails), I would highly recommend doing all 6 things on this list.
Got it. What else can I do?
Lots and lots. Siraj Datoo published a really good list on Quartz called The complete guide to not being that idiot who got the company hacked. This list is good for the home as well. I would encourage you to read the whole post, but here are the bullet points:
-
Install HTTPS Everywhere in your browser. (Switches to secured HTTPS traffic for several popular sites, among other things.)
-
Put a password on your home Wi-Fi. (Also: Use the
WPA2security mode.) -
Put passwords on all your devices. (Quit butt-dialing me like my friend Lindsey.)
-
Employ two-step authentication on everything. (We already covered this.)
-
Encrypt your laptop’s hard drive, especially if it’s a Mac. (It’s really easy on a Mac. System Preferences → Security → FileVault.)
-
Never send or save your password electronically. (Email, IMs and other forms of electronic communication leave a trail. Don’t be the weakest link.)
-
Use 1Password or a similar service. (We already covered this.)
-
Read your emails carefully to avoid phishing attempts.
-
Take precautions when you use an open Wi-Fi network. (Anybody can connect to an open network and listen for unsecured web traffic to figure out your secrets. This is a very easy thing to do.)
-
Know which applications are connecting to the Internet. (If you have a Mac, Little Snitch is a worthwhile investment.)